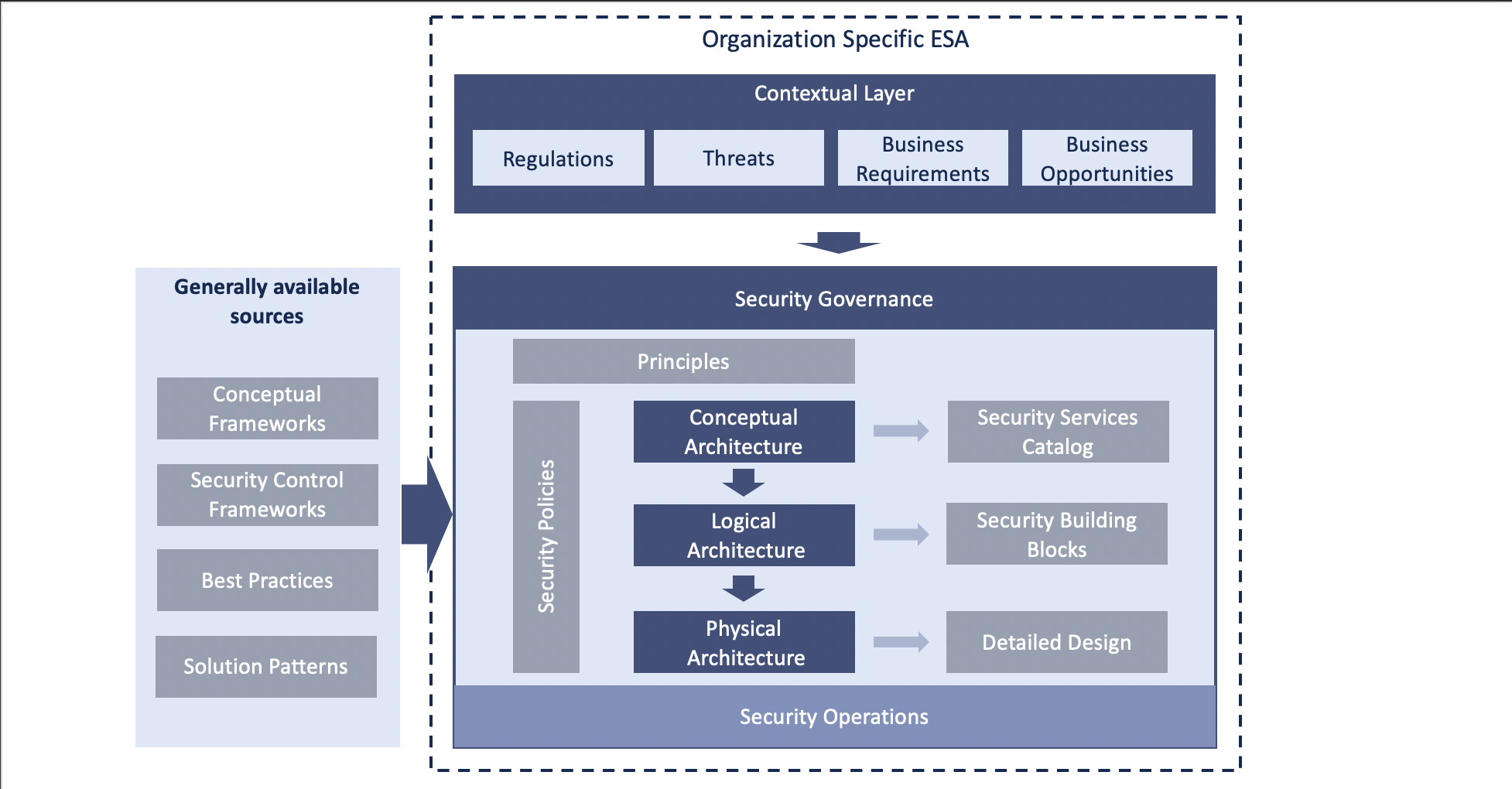
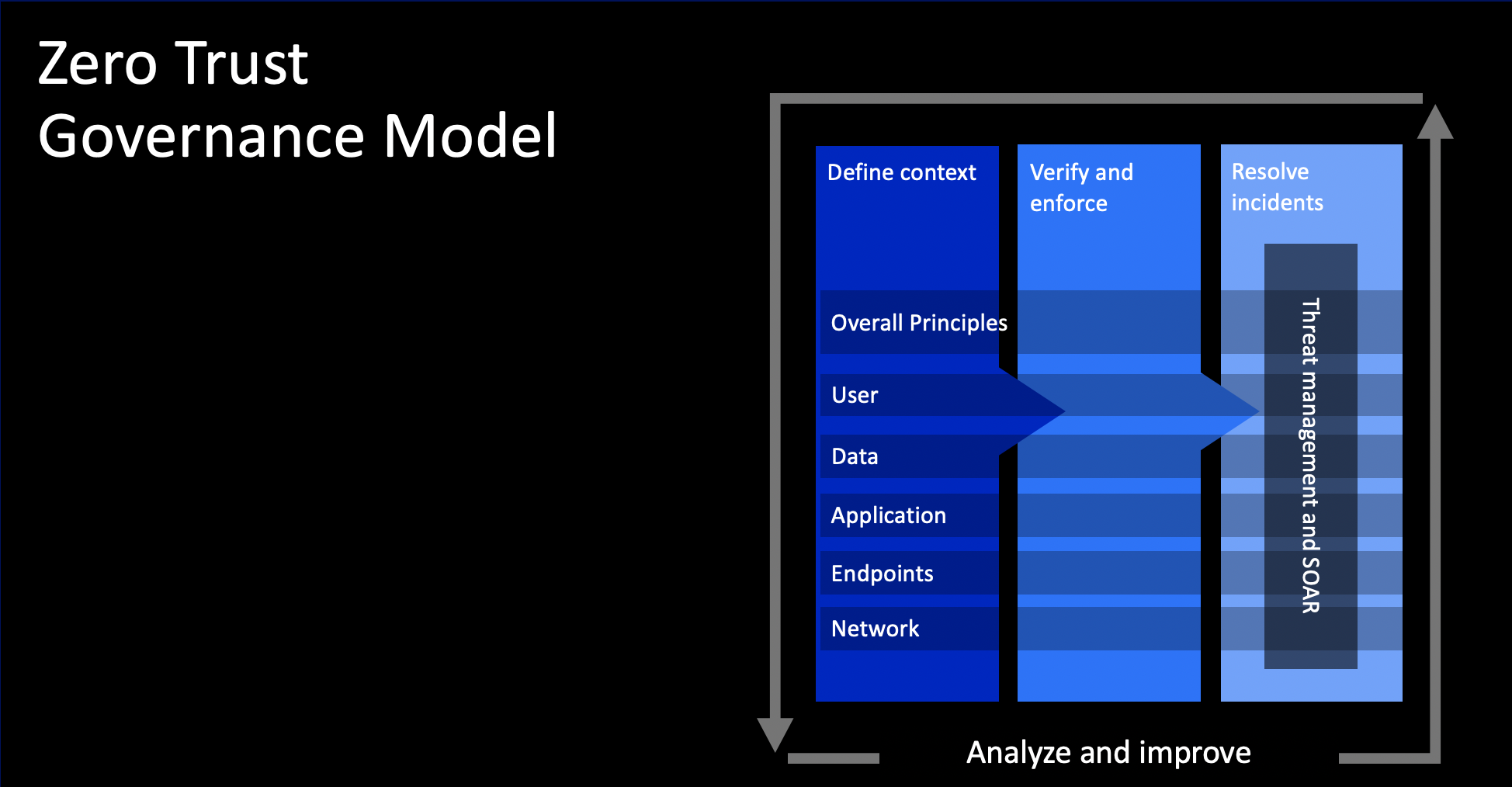
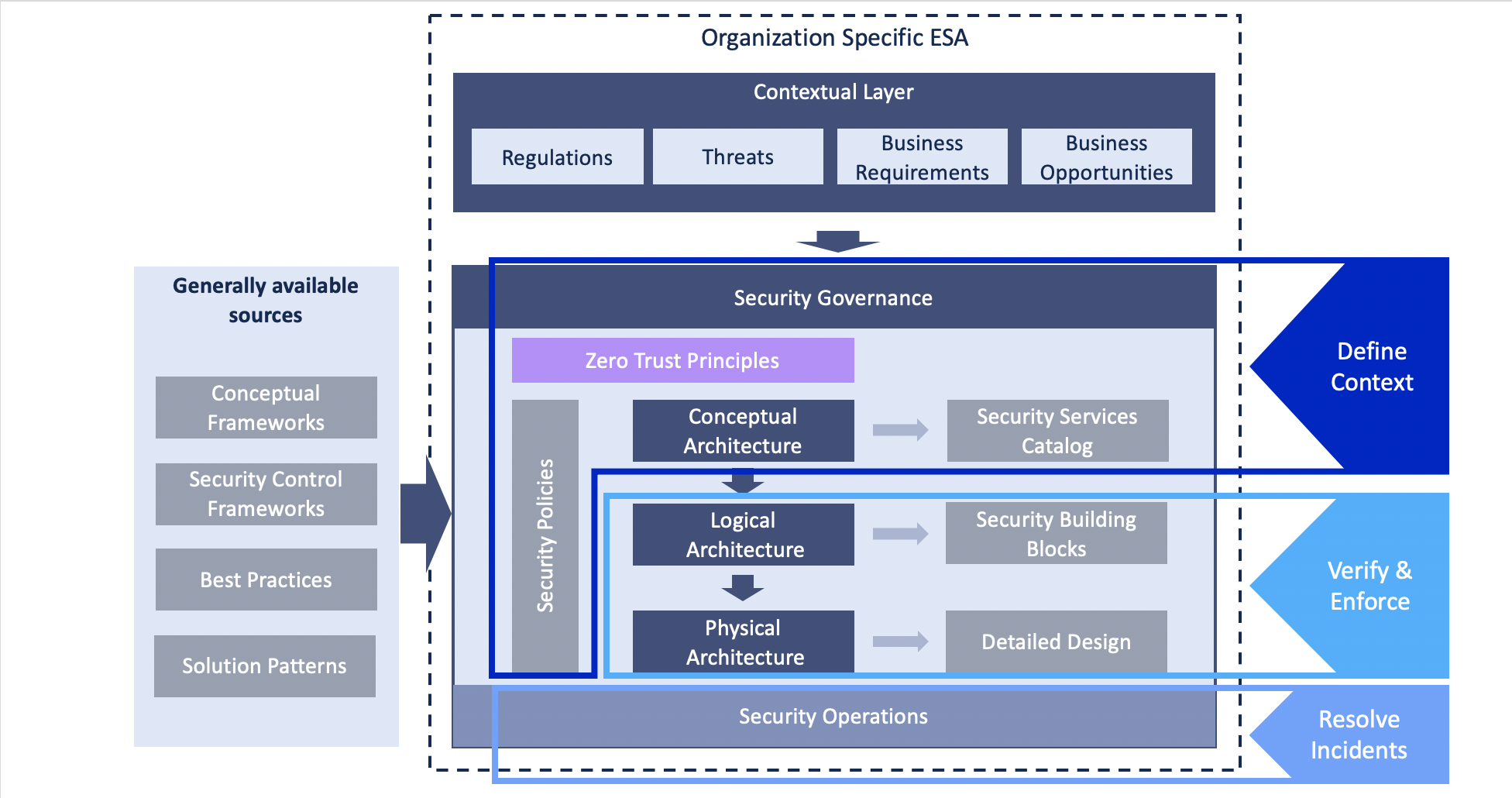
The recent Kaseya ransomware attack is yet another reminder of the voracity of the war cybercriminals are waging on the business world. In 2020, scan-and-exploit became the top initial attack vector for surveyed organizations, surpassing phishing, according to the 2021 IBM X-Force Threat Intelligence Index. The report noted manufacturing as the second-most attacked industry in 2020 for respondents. This is an increase from eighth place the year prior, and second only to financial services.
What’s behind these attacks?
Companies have invested a great deal in building castle-and-moat protections against external threats, focusing on protecting the DMZ or perimeter zone. In a world of known threats and less sophisticated techniques, this protection model worked reasonably well. But times have changed.
Cybercriminals can be well resourced and tenacious and even backed by nation-states. They can leverage evermore sophisticated tools, such as Ransomware-as-a-Service. These tools can be incentivized by cryptocurrencies with their strong liquidity and poor traceability. As a result, they are well positioned in the arms race against traditional perimeter defenses. Clearly, it is time to consider a zero trust approach to help protect your most valuable resource—your data.
The rise of zero trust
The problem with the castle-and-moat model is the primary focus on external defenses. Once inside, cybercriminals can generally move freely around without much impediment and wreak havoc. This has led to a broadening of the security perspective to encompass internal security, with what is termed the zero trust model.
The Biden administration in the United States, recently issued an Executive Order calling for advancement towards a zero trust model within the federal government and among federal contractors. Subsequently, in response to multiple high-profile ransomware attacks, the White House also issued a memo to business executives urging them to protect against the threat of the ransomware. Such a model is an “evolving set” of concepts that move beyond “defenses from static, network-based perimeters” according to the National Institute of Standard and Technology (NIST).
What happens when a cybercriminal or organization has breached a perimeter and has access to your secure environment? Typically, they will start a stealth scan to build a map of your network. They enumerate the server they are on for all its credentials and then try those credentials on your other servers to travel laterally. Most breaches move from computer to computer over standard protocols such as SSH, FTP, SFTP, HTTP, and HTTPS. This means you need to have a strategy for restricting the spread or movement within your organization.
Zero Trust Protects File Transfers
At IBM, our Sterling Secure File Transfer (SFT) solution is designed to align with a zero trust approach and harden servers to help reduce the possibility for ransomware or malware to travel laterally. The aim is to protect the inside of the castle – or inside the DMZ. Ultimately safeguarding internal intellectual property and assets. A zero trust approach requires securing and regulating movement between internal computers and servers and we begin by removing untrusted protocols.
Our SFT solution is designed to include IBM Sterling Connect:Direct which uses a security-hardened protocol. When malware reaches out internally, it will not know how to ‘talk’ to the protocol. It can also check the IP address from the server that has requested access. If that IP address is not on the internal list of trusted servers, which can be consistently updated, the receiving server automatically drops the session.
Connect:Direct can have additional checkpoints to further help prevent the spread of malware to another server. The malware also needs the correct credentials, which can be increased for additional protection of high-value servers. Also, only files with a specified name may be transferred.
Each server that uses Connect:Direct becomes a checkpoint – and choke point – for malware. This zero trust approach in Connect:Direct hardens infrastructure. It includes capabilities for zero trust practices for communications that can help mitigate risks of traditional protocols using FTP, SFTP and SSH. SFT can also encrypt data at rest. In transit, it provides multifactor authentication helping implement a zero trust strategy for your file transfers.
Do you have a traditional castle-and-moat security model? I urge you to consider implementing or expanding your zero trust strategy. It will help protect what is most valuable inside of your organization. You can start small and add more protections over time. The key is to begin now because the war will continue to escalate.